// introduction:-
Netmask is another simple tool which does one thing and that is, makes a ICMP netmask request. By determining the netmasks of various computers on a network, you can better map your subnet structure.
// How to open
Application →Kali Linux → Information gathering → Route Analysis → netmask
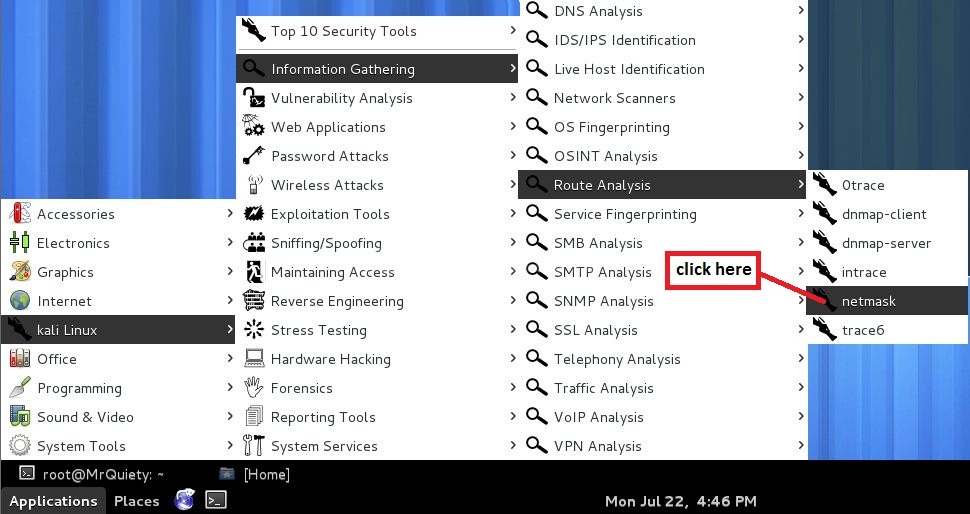
// OR
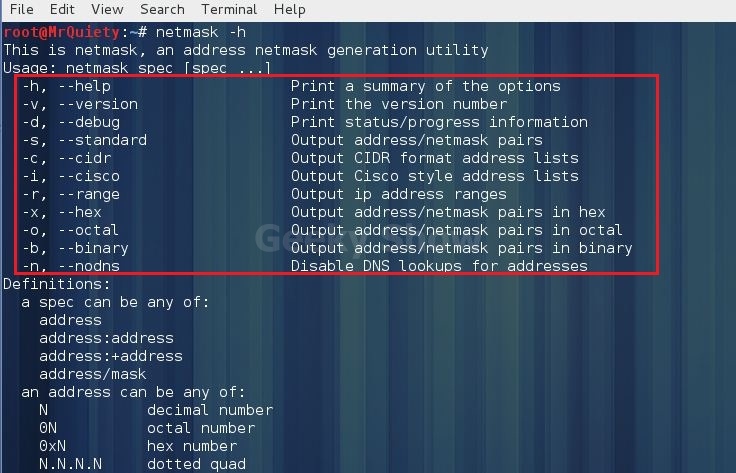
Open Terminal type netmask –h this command will open netmask with help options

Ex :- netmask –s 192.168.71.13
that's it
image by :-geeky show
Netmask is another simple tool which does one thing and that is, makes a ICMP netmask request. By determining the netmasks of various computers on a network, you can better map your subnet structure.
// How to open
Application →Kali Linux → Information gathering → Route Analysis → netmask

// OR
Open Terminal type netmask –h this command will open netmask with help options

2. netmask –v :- This command is used to visit netmask version
which is installed in your system.
Syntax:- netmask –v

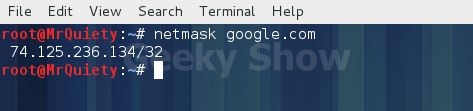
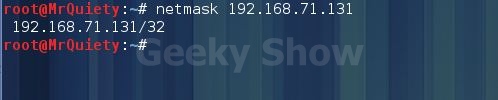
3. This is default search for a domain or IP.
Syntax:- netmask domain/IP
Ex :- netmask google.com

Ex :- netmask 192.168.71.131

4. Output
address/netmask pairs
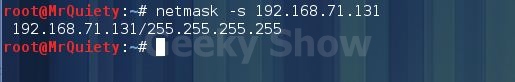
Syntax:- netmask –s domain/IP
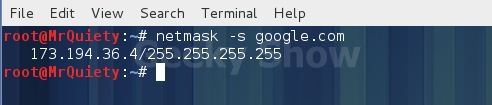
Ex :- netmask –s google.com

Ex :- netmask –s 192.168.71.13

5. Output CIDR format address lists
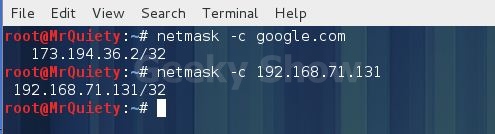
Syntax :– netmask –c domain/IP
Ex :– netmask –c google.com
E :– netmask –c 192.168.71.131
 \
\

6. Output Cisco style address lists
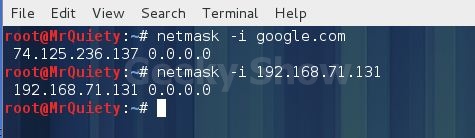
Syntax :– netmask –i domain/IP
Ex – netmask –i google.com
Ex – netmask –i 192.168.71.131
 \
\
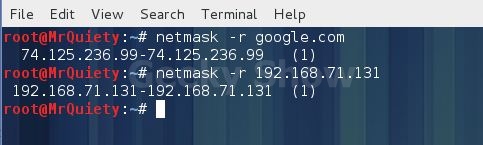
7. Output ip address ranges
Syntax – netmask –r domain/IP
Ex – netmask –r google.com
Ex – netmask –r 192.168.71.131

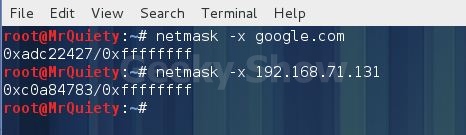
8. Output address/netmask pairs in hex.
Syntax – netmask –x domain/IP
Ex – netmask –x google.com
Ex – netmask –x 192.168.71.131

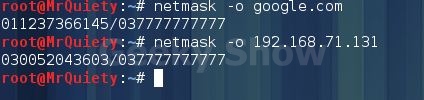
9. Output address/netmask pairs in octal.
Syntax – netmask –o domain/IP
Ex – netmask –o google.com
Ex – netmask –o 192.168.71.131

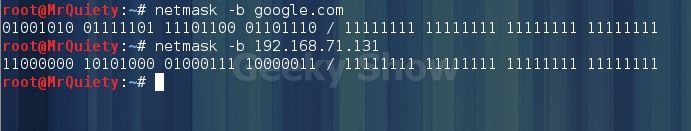
10. Output address/netmask pairs in binary
Syntax – netmask –b domain/IP
Ex – netmask –b google.com
Ex – netmask –b 192.168.71.131

that's it
image by :-geeky show
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com