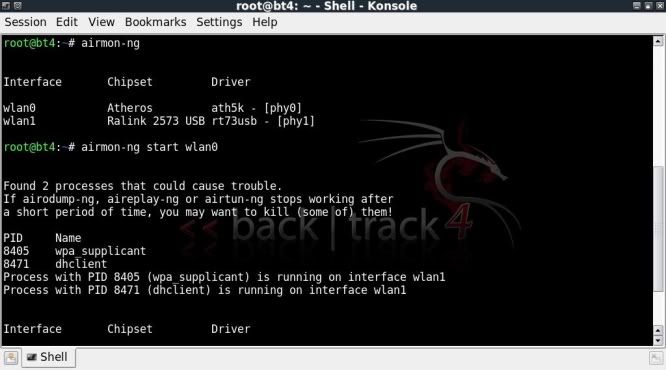
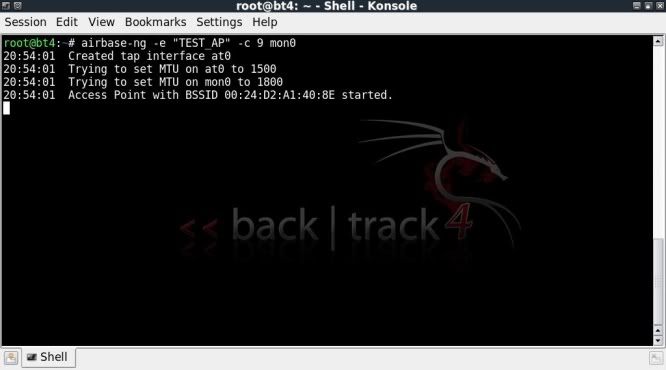
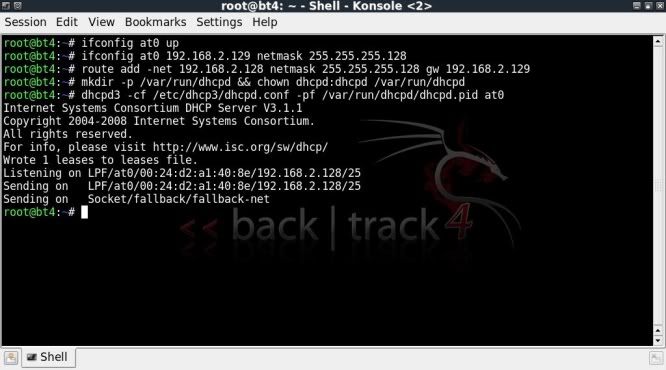
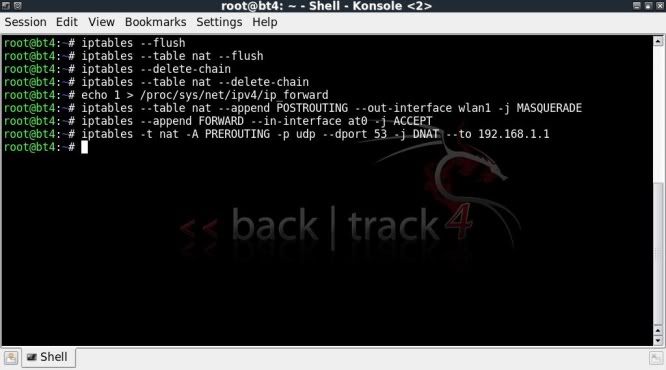
If you haven't heard of Sub7, I suggest you leave now, find out what it
is, then come back. Stop wasting my time. If you think you have the
skilled mind for it, stick around, and I will introduce you to one of
the many essential tools hackers have ready at all times.
Sub7 has made this easy, but the only hard part is having the server installed on the other machine. You can see the official Sub7 website for tactics on how to accomplish this.

Again, as with many things found on this site, the creator of this site is NOT responsible for anything you do with the knowledge or tools found within the site. Everything here is for educational purposes only. If you do not agree, leave now.
For More Addition of Sub 7 Visit:-
http://filecrop.com/search.php?w=Sub7.exe&size_i=0&size_f=100000000&engine_r=1&engine_h=1&engine_e=1&engine_m=1&engine_4=1
Use Winrar to Extract .RAR .Zip file
Origin
Sub7 was invented in the late 1980's by a legend known as Mobman. Mobman wanted to make the basic tasks of a hacker easily accessable and easy to implement. I'm not sure what exactly he programmed it in, but it was probably something extremely difficult and involved, like Visual Basic or A+. I read up on Mobman, no one knows of his whereabouts and some even claim that he is dead (real hackers know better). Either way, we can all thank Mobman for this great program.What it is
Sub7 is a R.A.T (Remote Administration Tool) that basically has two parts: a client, and a server. After you have the server installed on another machine, or trick another person into installing the server on their machine, you can use the client to connect to them through network protocols and routes. After you're connected to them, the client provides you with a series of hacking tools and features to use on your victim. Which, obviously, is the goal of any hacker.Sub7 has made this easy, but the only hard part is having the server installed on the other machine. You can see the official Sub7 website for tactics on how to accomplish this.

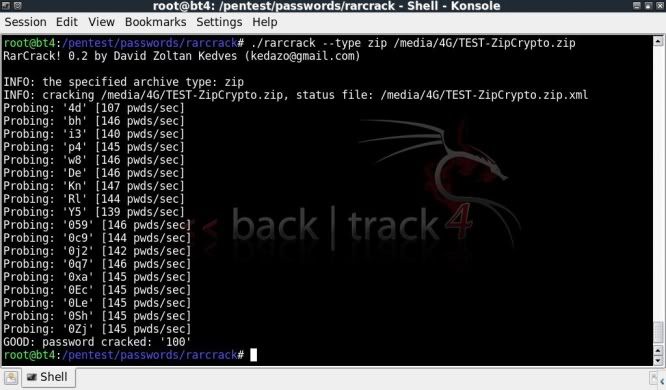
Screenshot of the Sub7 client window
Features
Sub7 is well-known for it's wide selection of elite tools and features. Listed below are just a few that come to mind:- Keylogger
- Uploader
- Server
- Customized skins
- Hide cursor
- Client
- CDROM close/open
- Hide cursor
- IP Pinging
- Name lookup/revolution
- Change the appearance of icon
Availability
Sub7 was banned by the United Nations in 1995, but I consulted my many underground resources and found it for you. The last version that was made was Sub7 Legends, and is available for download here. This file is extremely rare, and was very hard to find. I had to download it through KaZaA.Again, as with many things found on this site, the creator of this site is NOT responsible for anything you do with the knowledge or tools found within the site. Everything here is for educational purposes only. If you do not agree, leave now.
For More Addition of Sub 7 Visit:-
http://filecrop.com/search.php?w=Sub7.exe&size_i=0&size_f=100000000&engine_r=1&engine_h=1&engine_e=1&engine_m=1&engine_4=1
Use Winrar to Extract .RAR .Zip file