I had a lot of trouble with this and only really was able to complete it with the help of Gitsnik & Nick The Greek on the Remote Exploit forums.. awesome help there guys ;)
The steps involved are basically ;
- Configure dhcpd.conf
- Start the fake ap with airbase-ng
- Configure IP tables to pass through to host internet
- Capture / Monitor network traffic with tool of choice
In this case my test setup is as follows ;
> Using back|track4 pre final
> Using WiFi dongle to create a connection to internet on wlan1 (through gateway 192.168.1.1)
> Using my netbook wireless card (Atheros) to create the fake ap
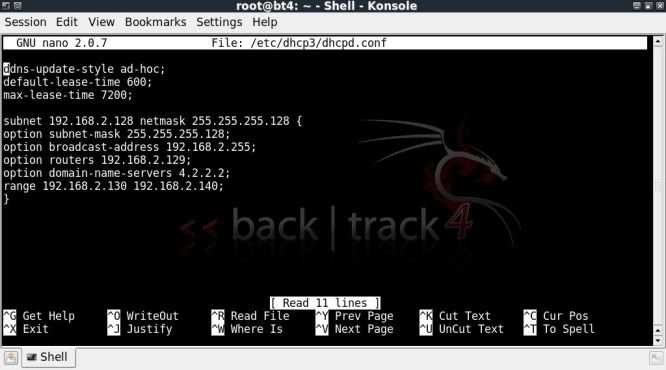
First to create/configure the dhcpd.conf file for later use ;
nano /etc/dhcp3/dhcpd.conf
ddns-update-style ad-hoc;
default-lease-time 600;
max-lease-time 7200;
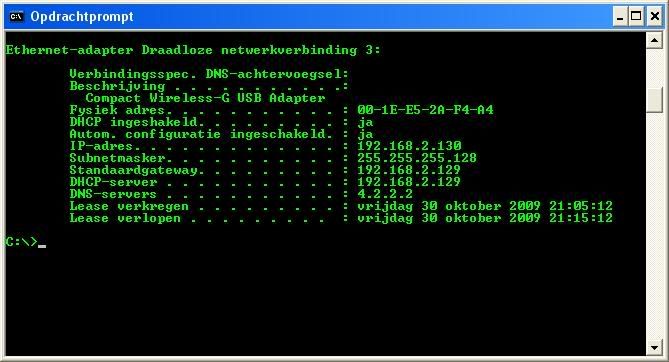
subnet 192.168.2.128 netmask 255.255.255.128 {
option subnet-mask 255.255.255.128;
option broadcast-address 192.168.2.255;
option routers 192.168.2.129;
option domain-name-servers 4.2.2.2;
range 192.168.2.130 192.168.2.140;
}
Ctrl X --> y --> Enter to save the file.
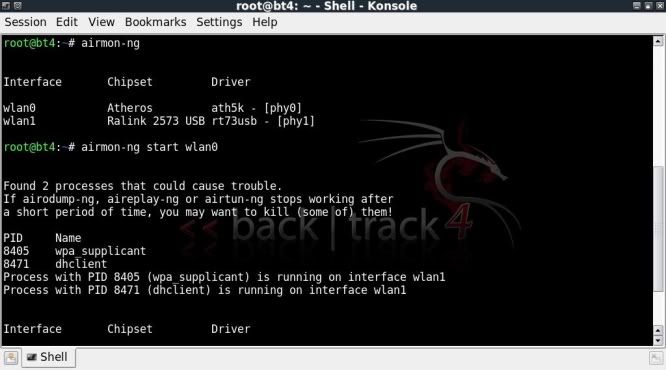
Then to start the fake ap with airbase, the interface needs to be in monitor mode ;
airmon-ng
airmon-ng start wlan0
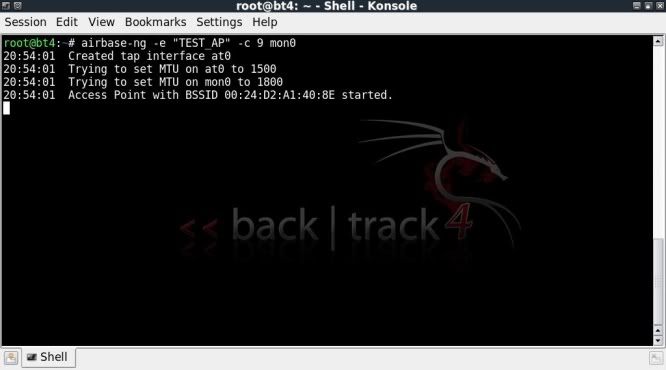
airbase-ng -e "TEST_AP" -c 9 mon0This will create a simple tap interface, on at0, with no encryption, on channel 9 and with the essid TEST_AP.

In this case I already had an internet connection up and running on wlan1, hence the warning messages, however this was of no further consequence.
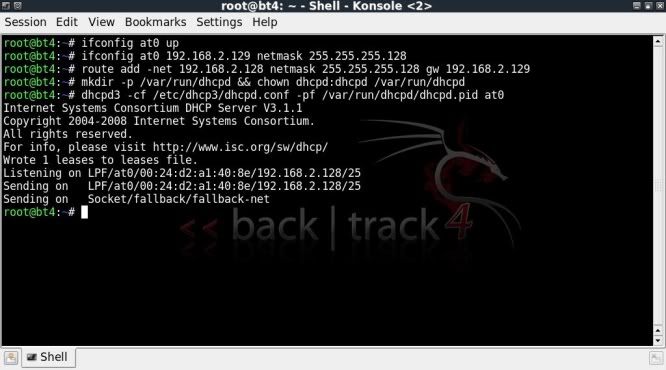
Then bring the interface up and assign subnet and gateway;
ifconfig at0 up
ifconfig at0 192.168.2.129 netmask 255.255.255.128
route add -net 192.168.2.128 netmask 255.255.255.128 gw 192.168.2.129
Then start DHCP, I was getting errors on the dhcpd settings, this is where the help came in :)
Needed to give further privilages to the dhcpd.
mkdir -p /var/run/dhcpd && chown dhcpd:dhcpd /var/run/dhcpd
Then to point the command to the alternative dhcpd.conf file and the alternative .pid file
dhcpd3 -cf /etc/dhcp3/dhcpd.conf -pf /var/run/dhcpd/dhcpd.pid at0
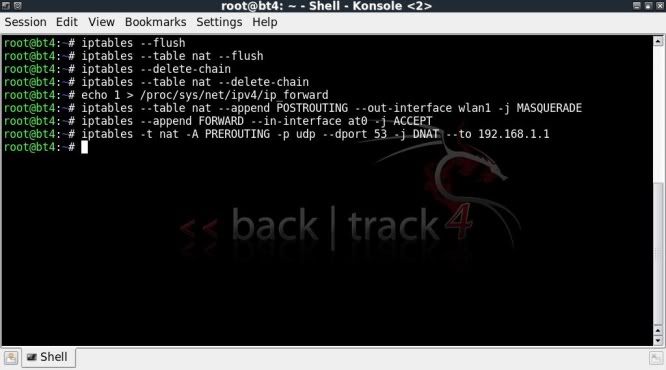
Then to setup the iptables to route the traffic through the tap interface to the internet connection (internet connection being the one wlan1 is connected to over my 192.168.1.1 gateway).
iptables --flush
iptables --table nat --flush
iptables --delete-chain
iptables --table nat --delete-chain
echo 1 > /proc/sys/net/ipv4/ip_forward
iptables --table nat --append POSTROUTING --out-interface wlan1 -j MASQUERADE
iptables --append FORWARD --in-interface at0 -j ACCEPT
iptables -t nat -A PREROUTING -p udp --dport 53 -j DNAT --to 192.168.1.1
Now basically you have a fake ap which people can connect to and browse the internet.. all through your connection.
Obviously this can be abused in any number of ways, all traffic can be captured and analyzed;
dsniff could be run on it together with urlsnarf, driftnet etc., sessions could be hijacked in real time..
So goes to show that you should be wary of free access points..

Do you need to increase your credit score?
ReplyDeleteDo you intend to upgrade your school grade?
Do you want to hack your cheating spouse Email, whatsapp, Facebook, instagram or any social network?
Do you need any information concerning any database.
Do you need to retrieve deleted files?
Do you need to clear your criminal records or DMV?
Do you want to remove any site or link from any blog?
you should contact this hacker, he is reliable and good at the hack jobs..
contact : cybergoldenhacker at gmail dot com